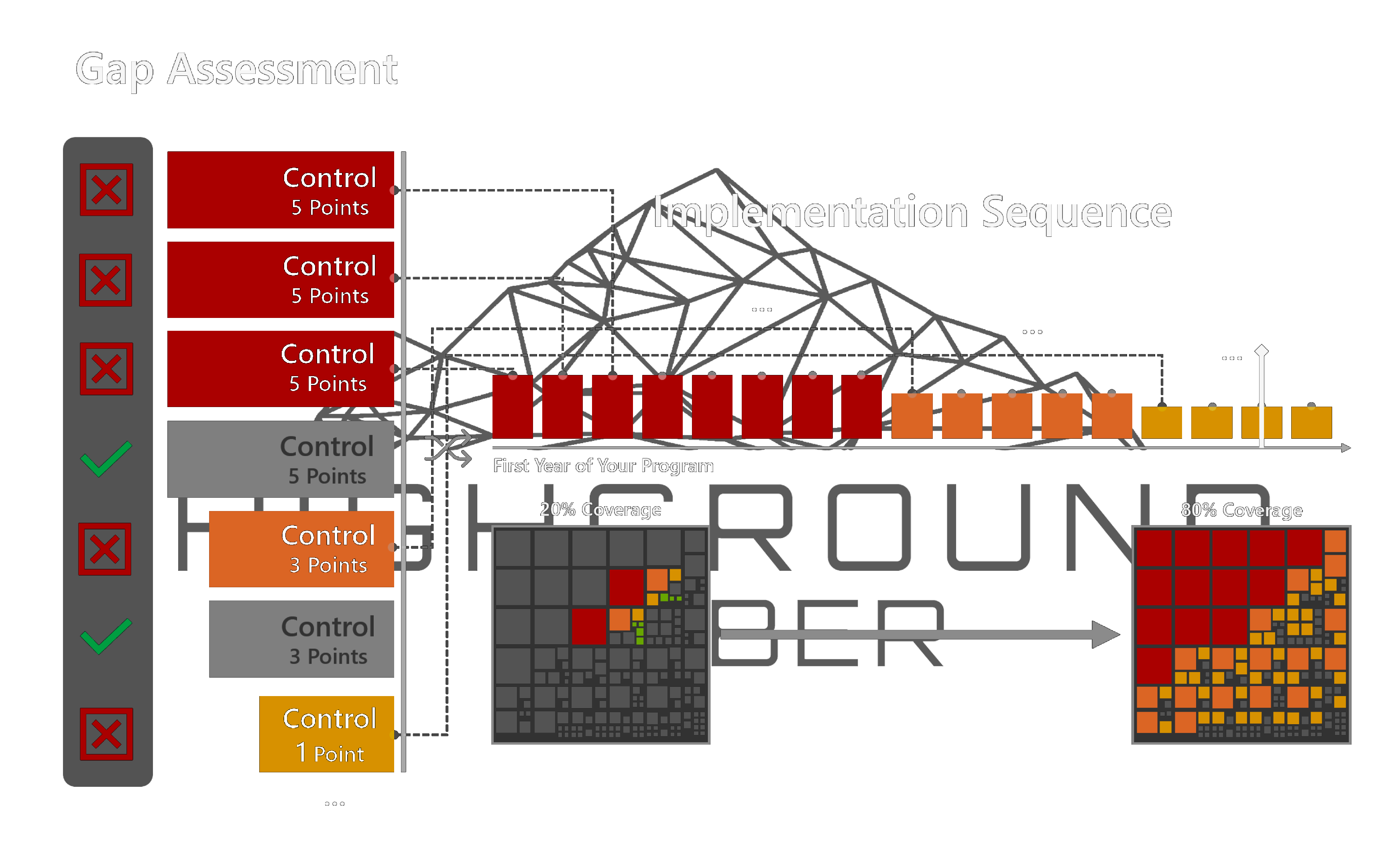
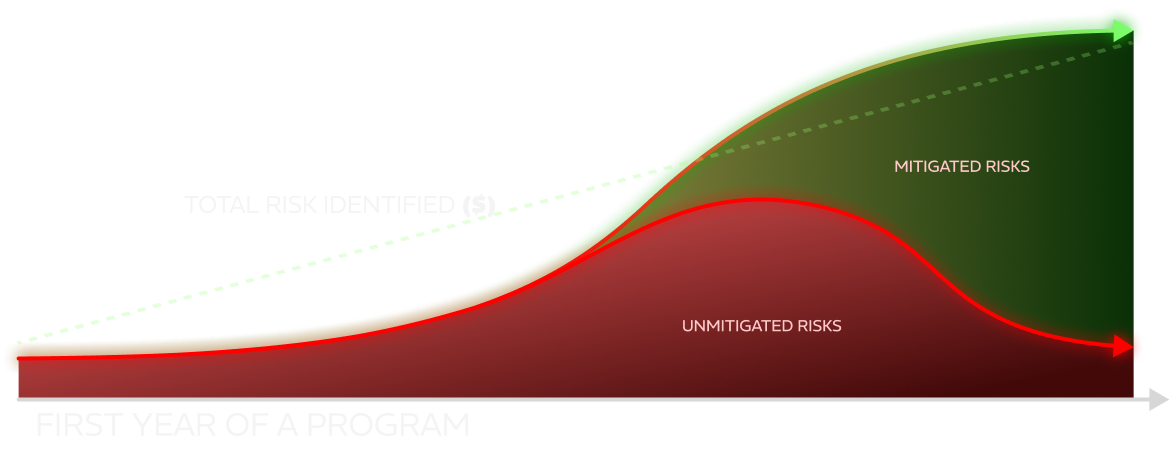
Acceleration through Prioritization
Practices in CMMC are assigned a criticality factor of one to five - and missing the mark on any practice with a weight of five is an automatic "hard failure" of your assessment. Once the gaps in implementation have been identified, we get to work addressing practices in their order of criticality to provide the most coverage in the least amount of time.
Optimization through Resource Reallocation

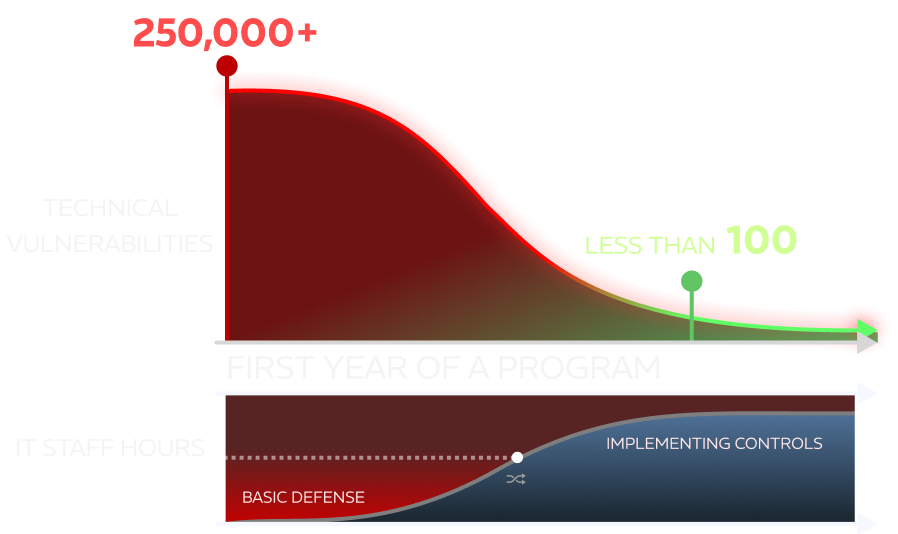













With a vast arsenal of intellectual property and processes available after a decade of implementing security frameworks, Highground also brings valuable man-hours to bear on your implementation activities. The lack of dedicated resources and expertise is no longer an obstacle in getting compliant. Highground knows what skills and subject expertise is required to make this journey in organizations of all sizes. We bring these skills and this knowledge as needed to get you where you need to be, helping you implement at every level of granularity.
We are not Managed Service Providers (MSPs). We are not Resellers. We are Assessment Preparation Professionals and Cybersecurity Practitioners. We have zero interest or allegiance to any particular solution beyond what is determined to be most effective for you at the enterprise architecture level. Assessors are barred from making value judgments regarding tools or providers used - so long as they have proven to satisfy controls. We uphold the same standard as consultants preparing you and your environment for assessment.
Execution Through Program Management
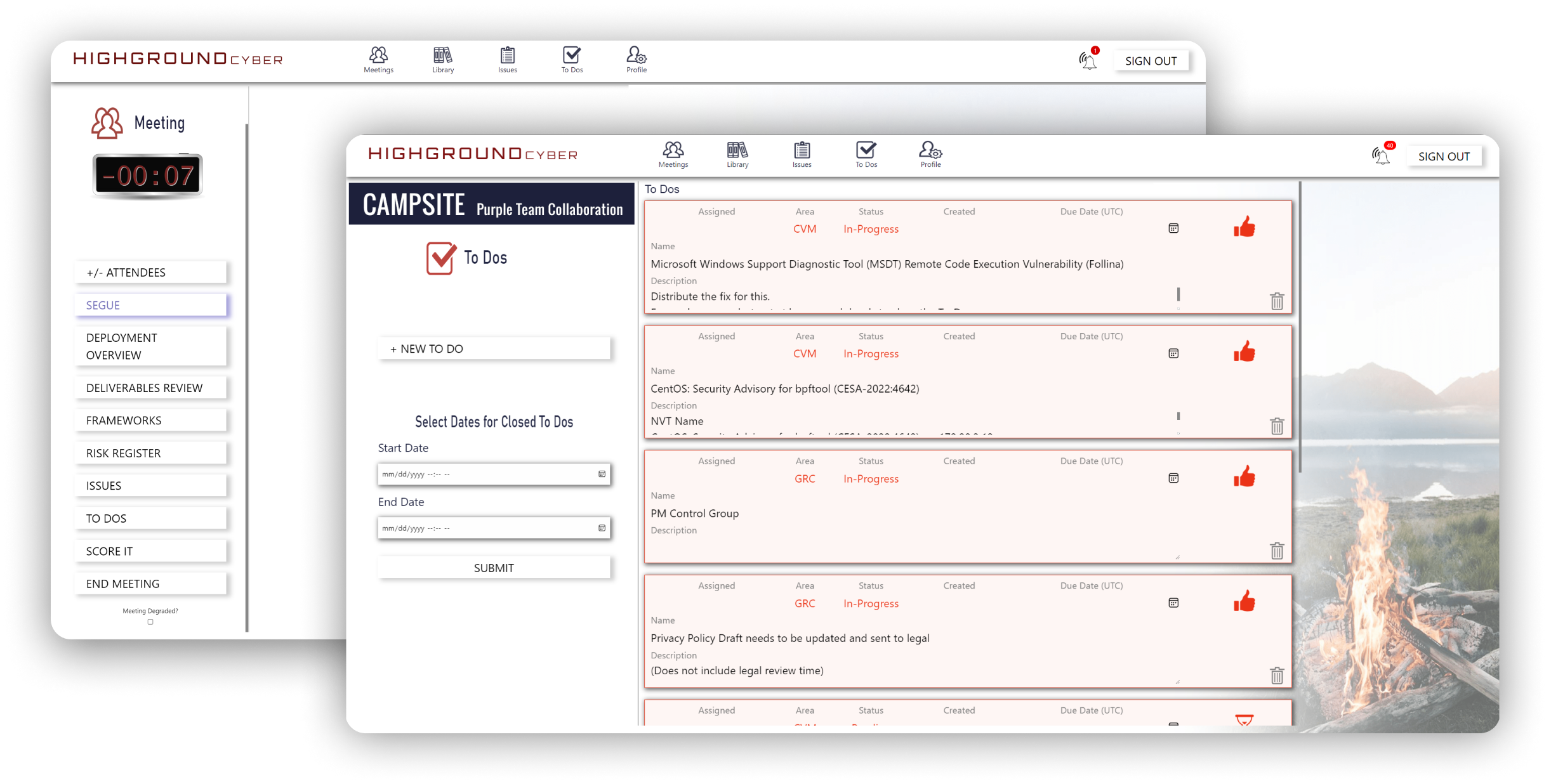
Based on Gino Wickman's TRACTION - Facilitate lean, incisive, and productive weekly L10 meetings that track tasks, identify issues, create alignment, and churn through work at faster speeds.
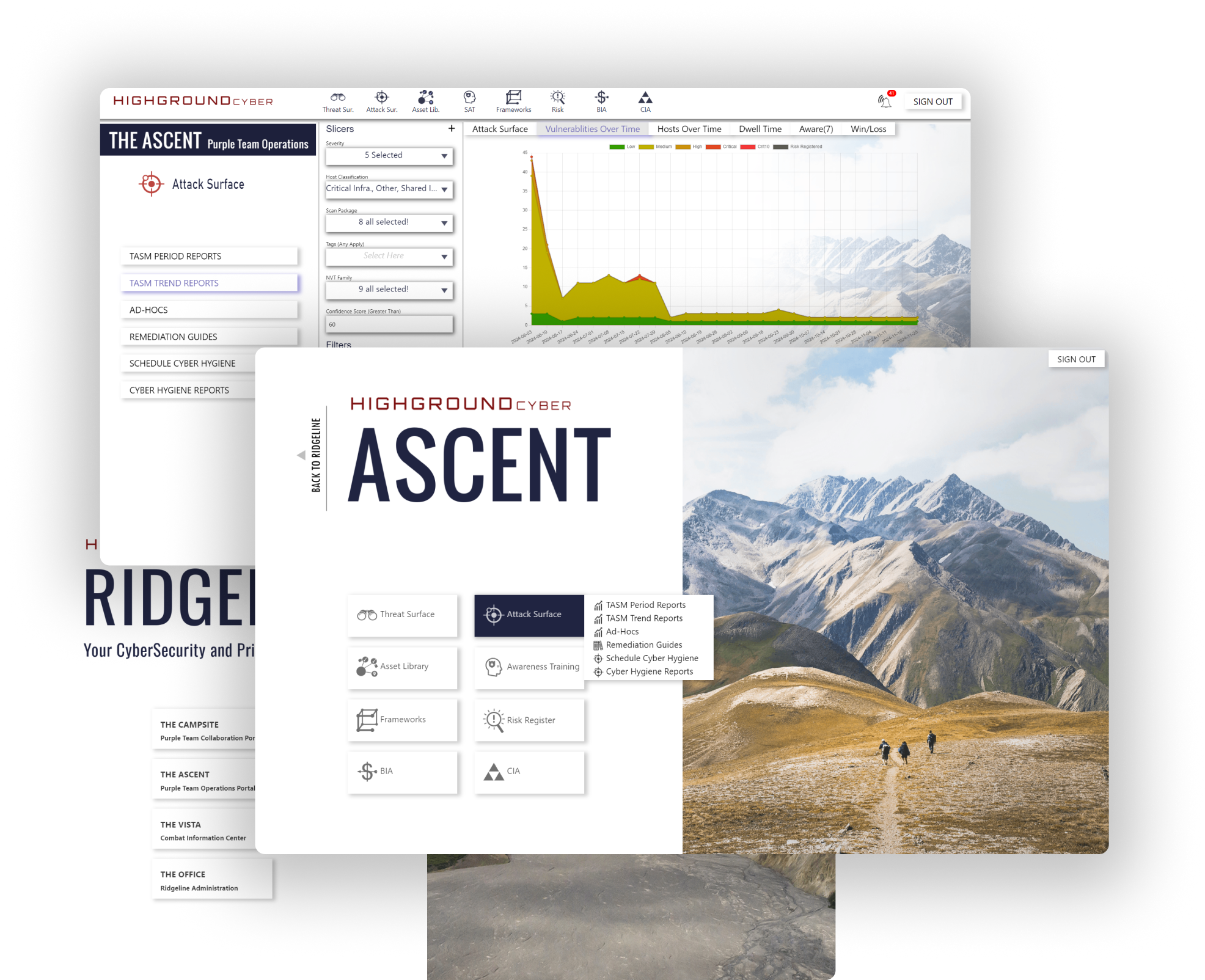
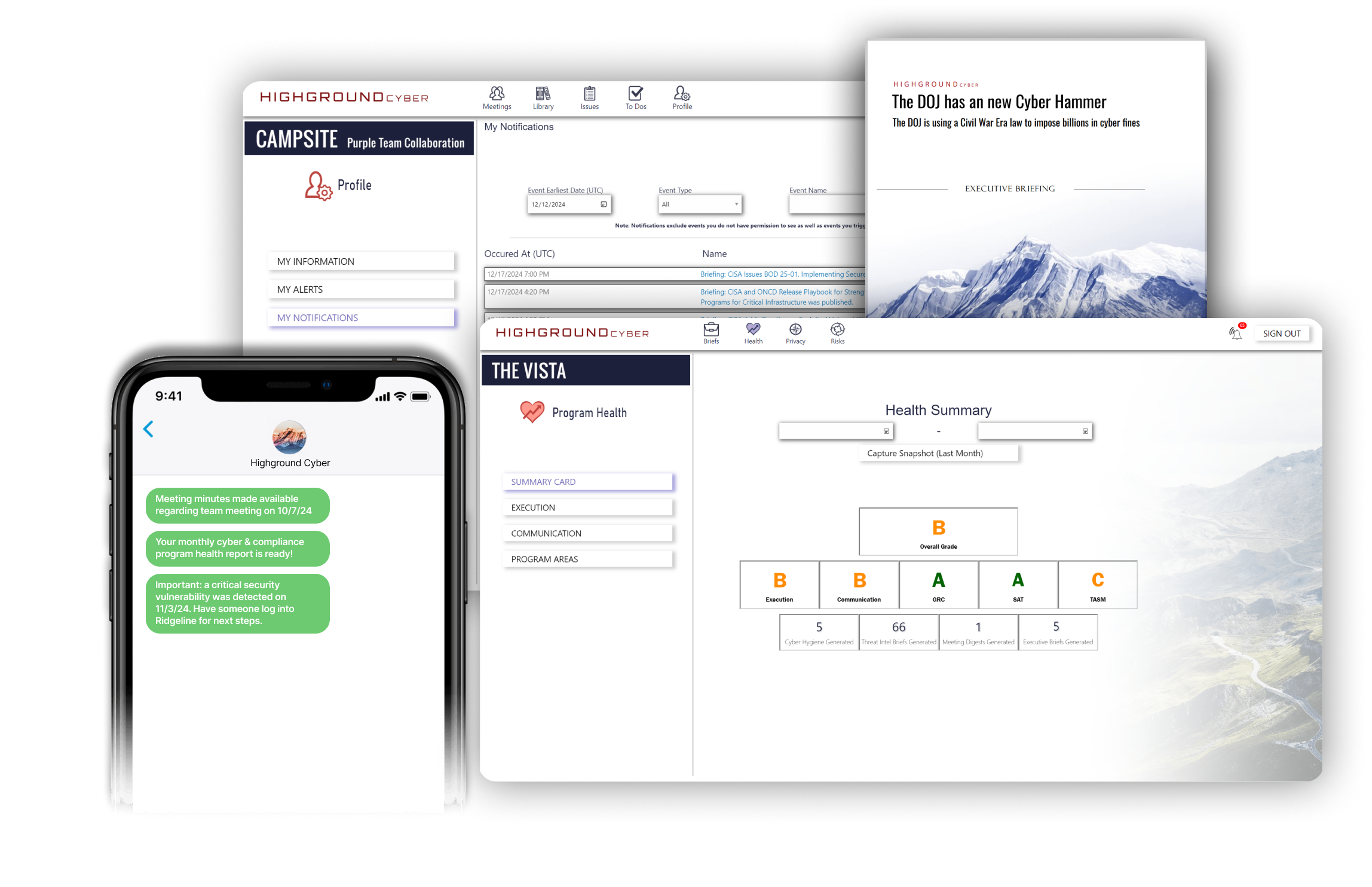
See your journey to the summit taking place at every level of operations. Experience the tangible impacts of every action with reporting on day-to-day activities, all the way up to quarterly and annual progress reports.
Get notified of new business risks that impact your program and monitor cyber-related risks to eliminate them from your business. Get real-time network-based vulnerability scanning of your assets to radically increase awareness and remove threats. All from one place.
Get notified with executive briefs on recent major cyber events - with analysis on its impacts to your company's strategic vision. See progress reports on your implementation of CMMC, and KPIs on program health for mutual accountability.